MemeCore (M) Digital Asset Theft Incident: On-Chain Forensics & OSINT Analysis Report
January 19, 2026
Introduction
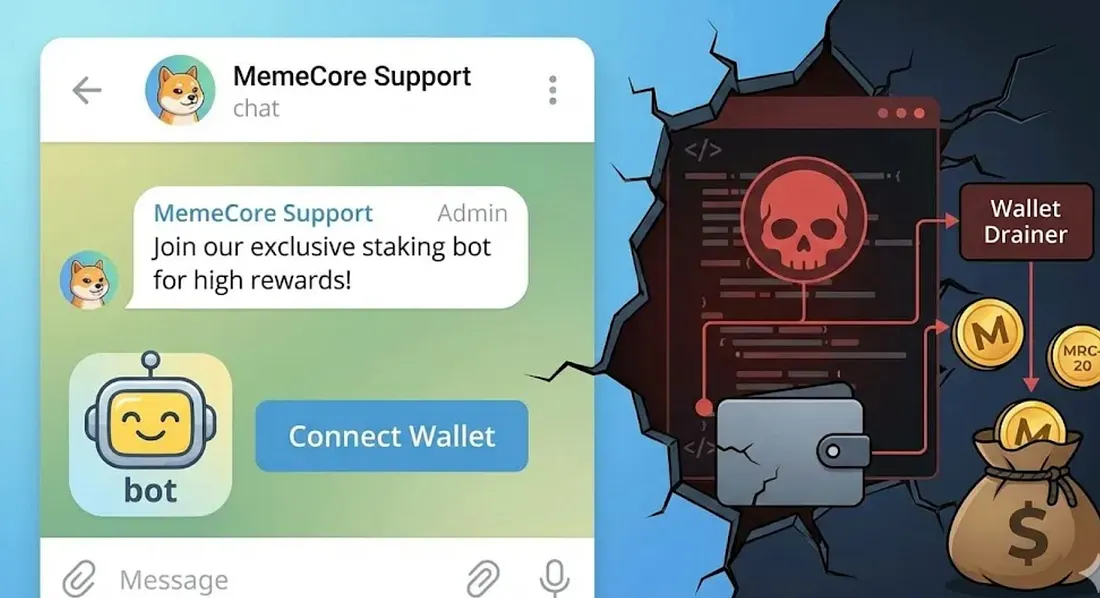
This report details a real-world case submitted by an applicant to ChainBounty's Victim Relief Program. The victim approached us after suffering a significant loss due to a targeted social engineering attack. ChainBounty is actively assisting the victim by providing comprehensive on-chain forensics and intelligence analysis to trace the stolen assets and identify the perpetrators for law enforcement purposes.
MemeCore (M) Digital Asset Theft Incident: On-Chain Forensics & OSINT Analysis Report
1. Executive Summary
This report synthesizes the results of on-chain forensic analysis and Open Source Intelligence (OSINT) investigation regarding the digital asset theft incident that occurred between December 7 and 8, 2025.
The incident appears to have originated from a social engineering attack targeting an active user of Memex, a major dApp in the MemeCore (M) ecosystem. The attacker impersonated community administrators and creators to lure the victim into a fake Telegram group, then induced them to connect their wallet to a fraudulent bot service using "high-yield staking rewards" as bait.
The victim created a new wallet and transferred assets as instructed, but the flow was designed to funnel funds into the attacker's scam network.
On-chain analysis reveals that the stolen funds did not end with a simple transfer. A multi-stage laundering flow was observed, involving MRC-20 token swaps within the MemeCore network, repetitive transactions based on the WM contract, cross-chain bridging via Meson Finance, inflows into Centralized Exchanges (CEX), and dispersed withdrawals across multiple exchanges.
Notably, a "direct-to-exchange" flow is clearly visible in the early stages. M tokens were directly transferred from the victim's wallet to Suspect Bitget Deposit 1 (0x7a5d...), and this fund was collected into the exchange's hot wallet (0x1ab4...) within a short period. This suggests the attacker operated a direct route to the exchange alongside other methods to accelerate cash-out early on.
The damage is calculated based on two criteria:
- Total M Token Outflow (Direct): 2,151.11 M, approx. $2,881.39 (Combined sum of direct transfers to exchange + EOA/Gathering Wallet).
- Total M Token Outflow (Including Bridge): 8,280.11 M, approx. $11,150.17 (Direct outflow + Meson bridge outflow included).
Furthermore, clues suggesting a connection to specific social accounts and developer community profiles were identified in Gathering Wallet 2 (0x1c00...5f), which was confirmed as a key hub for money laundering. Based on this, grounds to narrow down suspect candidates have been partially secured. However, this is a circumstantial judgment based on the correlation between public information (OSINT) and on-chain data, and is not a legally confirmed conclusion.
1.1 Summary Statistics
The key flows are summarized as follows:
1.2 Summary of Key Flows (4 Core Paths)
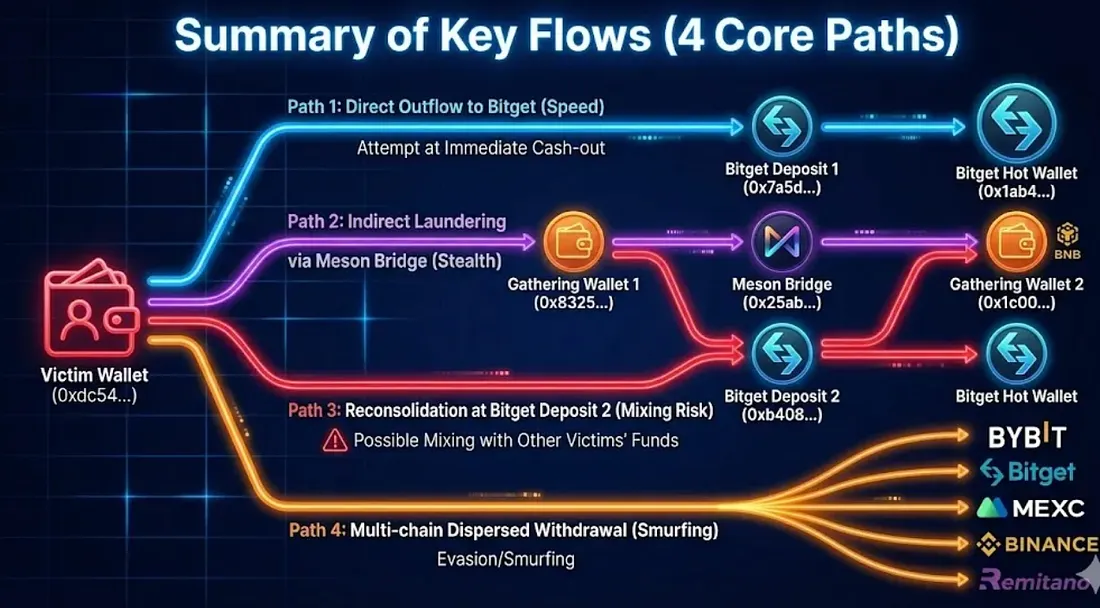
Path 1: Victim → Direct Outflow to Bitget (Attempt at Immediate Cash-out)
- A total of 2,140.72 M (approx. $2,867) was directly transferred from the Victim Wallet (0xdc54...) to Suspect Bitget Deposit 1 (0x7a5d...).
- The deposit was collected into the Bitget exchange hot wallet (Bitget 6, 0x1ab4...) within minutes (approx. 3-5 mins).
- This flow represents the attacker sending "M tokens that are easy to cash out immediately" straight to the exchange.
Path 2: Victim → Gathering Wallet 1 → Meson Bridge → Gathering Wallet 2 (Mainstream of Indirect Laundering)
- After WM contract processing, 5 types of MRC-20 tokens were received by the Victim Wallet and then drained to Gathering Wallet 1 (0x8325...e6).
- In Gathering Wallet 1, MRC-20s were swapped back to M, and 6,129 M was bridged via Meson Finance (0x25ab...48d3).
- 6,122.87 M arrived at Gathering Wallet 2 (0x1c00...5f) on the BNB Chain.
Path 3: Gathering Wallets 1, 2 → Reconsolidation at Bitget Deposit 2 (Possible Mixing with Other Victims' Funds)
- 900.65 M from Gathering Wallet 1 and 5,007.02 M from Gathering Wallet 2 flowed into Suspect Bitget Deposit 2 (0xb408...).
- The combined total is 5,907.67 M. As there is a "possibility of other victims' funds being mixed," this needs to be interpreted separately from the victim's sole damage amount.
- Subsequent collection into Bitget 6 (0x1ab4...) was confirmed.
Path 4: Multi-chain Dispersed Withdrawal from Gathering Wallet 2 (Evasion/Smurfing)
- From Gathering Wallet 2, after swapping M → BNB, there is a record of 37.51 BNB being dispersed and withdrawn in 48 transactions to 5 exchanges: Bybit, Bitget, MEXC, Binance, and Remitano.
- Activity of the same address was confirmed on Arbitrum and Base as well as BNB, reinforcing the cross-chain laundering pattern.
2. Incident Mechanism and Psychological Analysis
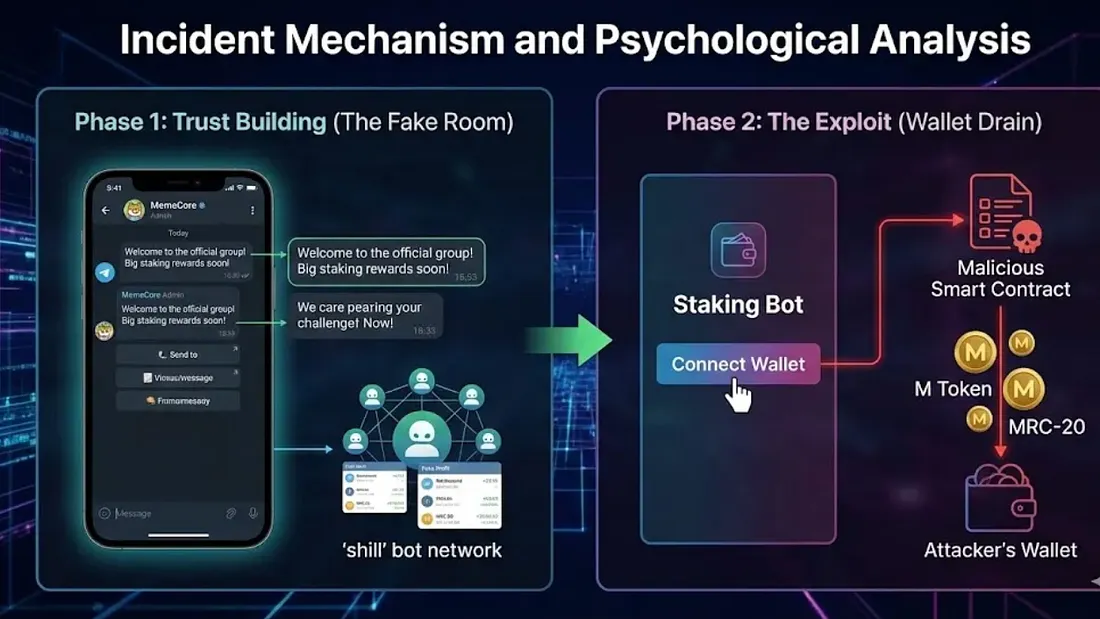
This incident appears to have started from a social engineering scenario targeting human trust rather than technical flaws such as system vulnerabilities. It seems to be a variation of the typical "Pig Butchering (Sha Zhu Pan)" tactic adapted to the MemeCore ecosystem context. There are indications that the attacker analyzed the community atmosphere and the victim's activity patterns beforehand to approach with a tailored script.
2.1 Manipulating the Environment to Build Trust: "The Illusion of the Fake Room" The attack seems to have begun with an approach from an account mimicking an acquaintance active on Memex. In anonymous messenger environments like Telegram, profile pictures and Display Names can be configured similarly, and Usernames (Handles) are hard to distinguish with just a one-character difference. The attacker was judged to have secured trust by exploiting these characteristics. The Telegram room the victim was invited to contained multiple accounts impersonating Admins and Creators. They staged the room to look like an "Official Community" by continuing conversations or sharing profit verification screenshots even before the victim joined. In such an environment, it was easy to mistake the room for an extension of the official Memex community, which became the basis for the fraud.
2.2 Technical Deception: Fake Bot and Inducing Wallet Connection Once a certain level of trust was established, the attacker guided the victim, saying, "You can receive staking rewards if you connect your wallet via the Telegram bot". The method is close to a typical Phishing or Drainer type. The wallet (0xDC54...69b) the victim newly created and connected was a "clean wallet" with almost no transaction history. The moment the victim trusted the instructions and moved assets, it is likely the attacker secured control through one (or a combination) of the following methods:
- Possibility that the transaction signed via the bot was actually an Unlimited Token Approval, not staking.
- Possibility that it was designed to execute an asset Transfer transaction during the signing or connection process.
- Possibility that keys or permissions were exposed to the attacker during the wallet creation/connection process. The key point is that "Wallet Connection" may have turned into an act of handing over actual asset authority, rather than simple login or authentication.
3. Technical Characteristics of MemeCore Ecosystem and Asset Structure
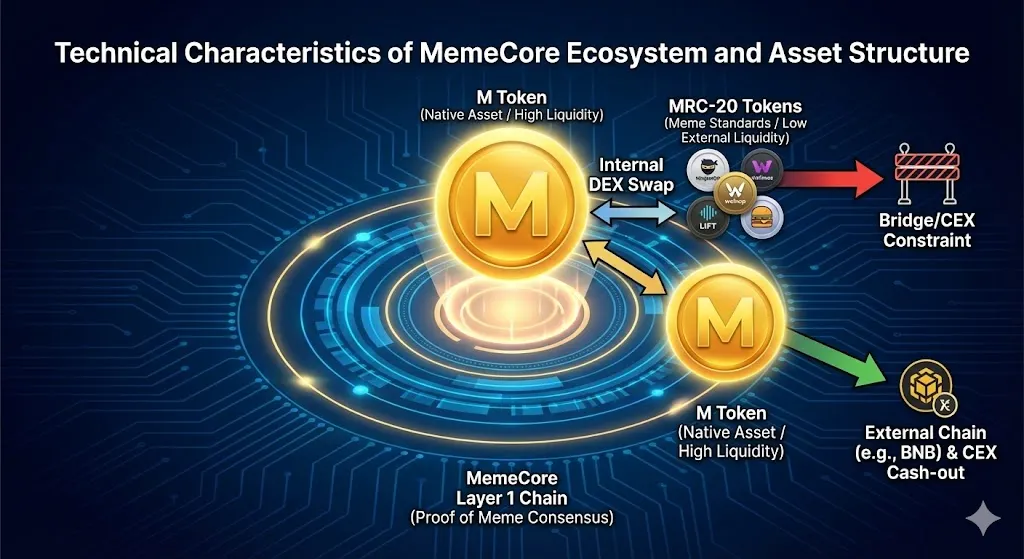
To interpret the fund flow, it is necessary to first understand the background of the MemeCore chain where the victim's assets existed and the asset structure. This explains why the attacker performed repetitive swaps and why the laundering path developed into a specific pattern.
3.1 MemeCore and Proof of Meme (PoM)
MemeCore is a Layer 1 chain aimed at connecting the cultural value of Memes with an economic reward structure. It promotes Proof of Meme (PoM) as its consensus structure, which includes elements like community contribution and viral activities in the reward system alongside simple staking. The base asset of this chain is the M token. M is used for core functions such as gas fees, governance, and validator staking, and has relatively high liquidity, which is why the attacker ultimately pooled funds into M for laundering.
3.2 MRC-20 Token Standard and Cash-out Constraints
Tokens such as NinjaMEX, walxop, LIFT, Bubger, and Abudium identified in the swap path of this incident follow the MemeCore-specific token standard (MRC-20). These appear to be "transit tokens" temporarily passed through during the process of the attacker exchanging stolen assets on the internal DEX, rather than assets originally held by the victim. Technically similar to ERC-20, they are structured for the creation and circulation of meme tokens within MemeCore. The issue is external compatibility. Since it is rare for external chains, centralized exchanges, or bridges to directly support MRC-20, it is difficult for the attacker to move them out externally and cash them out in the MRC-20 state. Eventually, to proceed to the actual cash-out stage, they must go through the flow of: converting back to M on the internal DEX -> moving to an external chain (BNB Chain, etc.) via a bridge -> attempting cash-out via swap/dispersed withdrawal on the external chain. The massive internal swap transactions observed in the report are interpreted as reflecting the constraint of having to convert back to M for external export, along with the possibility of transit swaps intended to confuse tracking in some sections.
4. Incident Timeline and Detailed Forensic Reconstruction

This incident is clearly divided into Reconnaissance & Testing on December 7 and the Main Exploit on December 8. The attacker checked the validity of the path the day before, and then stole all available assets and proceeded with rapid laundering the next day.
4.1 Phase 1: Reconnaissance and Initial Infiltration (Dec 7) – Traces Left by Destination Choice Immediately after securing access rights, the attacker showed a pattern of verifying two things with small (or relatively small) transfers first, rather than moving the full amount immediately:
- Whether the wallet is actually usable by the attacker.
- Whether the exchange deposit is processed normally (no risk of detection/blocking). At 10:18 UTC, 388.717 M was transferred to Bitget Deposit 1 (0x7a5d...), and at 14:08 UTC, an additional 752 M was transferred via the same path. This flow aligns with the typical pattern of a small test followed by additional transfers. The notable point is that the receiving address 0x7a5d...337 is estimated to be a User-Assigned Deposit Address of a Centralized Exchange (Bitget), not a personal wallet. Funds flowing into this address were observed being collected into the Bitget hot wallet (0x1ab4...f23) within minutes. If cooperation with the exchange is established, there is a possibility that tracking can continue on an account basis (KYC-based).
4.2 Phase 2: Full-Scale Asset Theft and Laundering (Dec 8) – Forced Conversion to M and Exfiltration The full-scale theft proceeded rapidly on December 8. In this phase, it is observed that repetitive processing of the WM contract and mass liquidation (swap) of MRC-20 tokens were carried out in parallel with simple transfers.
- 4.2.1 WM Repetitive Processing Pattern: Between 06:45 and 06:49 UTC, 8 repetitive transactions occurred against the WM contract, confirming processing (Deposit/Withdraw) of approximately 8,000 M. This repetitive wrapping/unwrapping can be interpreted as (1) a staging to confuse tracking, or (2) a preparatory step to match the asset form required for subsequent swaps/bridging.
- 4.2.2 Organized Outflow of 5 MRC-20 Tokens and Immediate Cash-out: Around 1:24 PM, continuous M→MRC-20 swap transactions via the internal DEX occurred in the victim's wallet, which appear to have been performed by the attacker. Subsequently, these 5 MRC-20 tokens were transferred to Gathering Wallet 1 (0x8325...eae6), where a process of converting them back to M via the Swap Router was observed. This choice is pragmatic from the attacker's perspective. The longer low-liquidity meme tokens are held, the greater the price fluctuation and tracking traces may become. It seems the attacker chose to quickly convert MRC-20 to M to increase mobility and cash-out potential.
4.3 Phase 3: Cross-Chain Bridging and Final Concealment – Attempt to Evade Tracking via Chain Hopping The secured M tokens did not stay in the MemeCore chain for long and were observed moving to the BNB Chain via the Meson Finance (0x25ab...48d3) cross-chain bridge.
- Meson Bridge: 6,129 M Deposited.
- BNB Chain Arrival: 6,122.87 M received at Gathering Wallet 2 (0x1c00...5f) (Approx. 3 mins to arrive). Gathering Wallet 2 subsequently acts as a hub to send funds to exchanges or disperse them to other chains (Base, Arbitrum). It has a strong character of a "Operational Wallet" used repeatedly rather than a simple transit point.
5. Fund Flow Structure Analysis
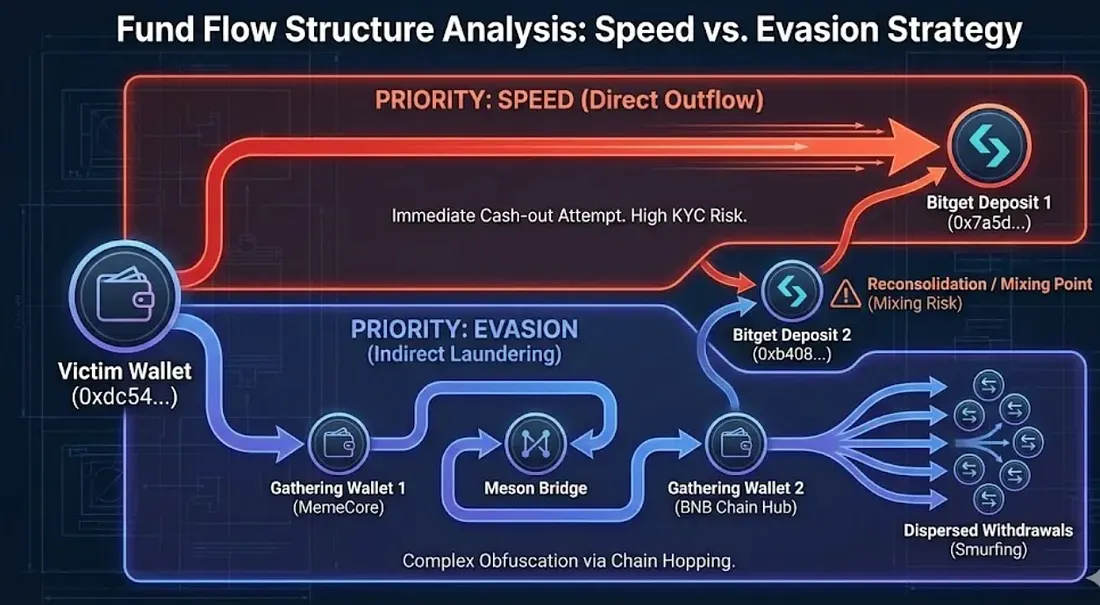
Funds drained from the victim's wallet moved largely in two directions:
- Direct Outflow straight to the exchange (Priority: Speed).
- Indirect Laundering via gathering wallets and bridges (Priority: Evasion).
5.1 Key Deposit (Receiving) Addresses
- Suspect Bitget Deposit 1:
0x7a5d...337/ Received: 2,140.72 M (~$2,867.47) / Note: Exchange Transfer. - Gathering Wallet 1 (MemeCore):
0x8325...eae6/ Received: 5 MRC-20s + 10.39 M / Note: MRC-20 → M Swap. - Gathering Wallet 2 (Multi-chain Same Address):
0x1c00...285f/ Received: 6,122.87 M & Multi-chain activity (BNB/Arbitrum/Base). - Suspect Bitget Deposit 2:
0xb408...dd5c/ Received: 5,907.67 M (~$7,969) / Note: From Gathering Wallets 1, 2 → Exchange. Caution: Possibility of mixing with other victims' funds.
5.2 Characteristics and Implications in Fund Flow First, the laundering strategy is split into two. Part of it prioritized speed by sending it quickly to the exchange (Path 1), while the rest tried to make tracking difficult through bridging and multi-chain dispersion (Paths 2, 4). Second, Bitget appears repeatedly. Both the direct outflow path (0x7a5d...) and the path from the gathering wallet (0xb408...) converge to Bitget deposit addresses. In particular, 0xb408... is a common point receiving funds from both Gathering Wallet 1 and Gathering Wallet 2, making it a candidate for a key cash-out window. However, as other victims' funds may be mixed in this section, definitive conclusions should be avoided. Third, Gathering Wallet 2 (0x1c00...5f) functions as a central node that receives bridged funds and then performs exchange transfers or dispersion to other chains.
5.3 Multi-Exchange Dispersed Withdrawal (Smurfing) Statistics (BNB Only) From Gathering Wallet 2 (BNB Chain) → Exchange Withdrawal Statistics:
- Bybit: 23.44 BNB / 16 txs
- Bitget: 7.15 BNB / 2 txs
- MEXC Global: 5.06 BNB / 22 txs
- Remitano: 1.30 BNB / 4 txs
- Binance: 0.56 BNB / 4 txs
- Total Exchange Withdrawals: 37.51 BNB / 48 txs / 5 Exchanges Note: After swapping M → BNB at Gathering Wallet 2, dispersed withdrawals were made to multiple exchanges. Activity of the same address was confirmed on Arbitrum and Base, reinforcing the cross-chain laundering pattern. Reference: Remitano is known as a platform widely used for P2P trading in Southeast Asia, which can serve as a reference clue for geographic profiling (Note: Do not conclude).
6. Relevant Actor Intelligence Analysis
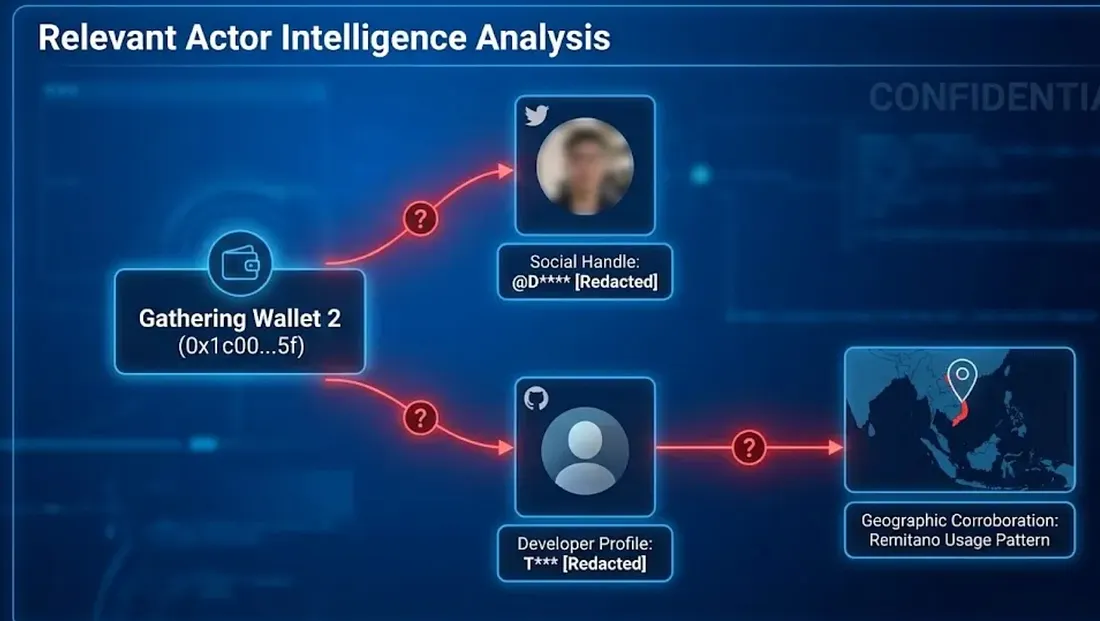
In this investigation, by cross-examining on-chain flows and off-chain public activity traces, we secured clues to narrow down the relevant Actor (Actor A) and associated account/profile candidates. The central address of the analysis is Gathering Wallet 2 (0x1c00...5f), and OSINT information was organized around this address.
6.1 Circumstances Connecting On-Chain Activity and Digital Identity In this case, some clues were observed where 0x1c00...5f, identified as a key gathering address, could be connected to external public activities. If the same address is repeatedly mentioned or exposed in specific social accounts or community profiles, it can serve as important evidence connecting on-chain addresses with off-chain activities. There are circumstances where a specific social account marked as (Redacted) posted the 0x1c00...5f address multiple times in posts related to past airdrops, whitelist registrations, faucet participation, etc. This raises the possibility that the address is associated with the account's activity to a certain level.
6.2 Detailed Identity Profile (Circumstantial) In the OSINT investigation, circumstances were confirmed where the social account/handle marked as (Redacted) is connected to a specific bounty/task platform (e.g., Superteam Earn) account/profile. The following additional information is derived from this:
- Real Name/Legal Identity: (Redacted)
- Country/Region of Residence: (Redacted; Partially consistent with Remitano usage patterns, etc.)
- Professional Identity: (Redacted; Based on self-introduction)
- Tech Stack Claims: (Redacted)
- Activity Character: (Redacted)
Additional Explanation: Meaning of "Partially Consistent with Remitano Usage Patterns" Here, "Partially consistent with Remitano usage patterns" does not mean concluding residence in a specific country/region (e.g., Vietnam) solely because Remitano appeared. It is intended to be referred to as a supplementary clue that increases probability from the perspective of Geo-profiling. specifically:
- Regional Character of Remitano: Remitano is known to be relatively widely used for P2P On/Off-ramp (cash-out/settlement) purposes in Southeast Asia (especially Vietnam) rather than being used equally worldwide like global major exchanges. Therefore, if Remitano is naturally included and repeatedly observed in the multi-exchange withdrawal flow, the possibility that the actor's living sphere/settlement environment touches the Southeast Asian region (including Vietnam) relatively increases.
- Hints form "Exchange Combination": In this case, regional P2P channels like Remitano appear alongside general-purpose exchanges like Bybit, Binance, and MEXC. This combination can be interpreted as a form often observed in dispersed withdrawals considering the final cash-out route, rather than simple investor propensity.
Therefore, Remitano traces are worth referencing as a "Geographic Clue Candidate". However, it is a "Supplementary Clue," not definitive evidence. Final confirmation must be made through cooperation/investigation data such as exchange KYC, login/access logs (IP/Device), and withdrawal methods (Bank/Payment info).
7. Conclusion & Our Commitment
Comprehensive Conclusion This incident, occurring on December 7-8, 2025, was a social engineering-based asset theft. Funds were laundered through two parallel paths:
- A direct path flowing straight into the Bitget exchange (Speed).
- An indirect path exfiltrated to external chains via the Meson bridge after internal swaps on MemeCore (Stealth).
Additionally, circumstantial evidence links "Gathering Wallet 2" (0x1c00...5f) to specific social accounts and developer profiles, providing strong identification clues for law enforcement.
Response Strategy ChainBounty has advised a phased response:
- Phase 1: Immediate reporting to law enforcement with key TxIDs and requesting asset freezing at Bitget.
- Phase 2: International cooperation review for cross-border tracking.
- Phase 3: Continuous monitoring of suspect addresses and community education on risk factors.
Need help tracking stolen funds? Recovering stolen assets starts with professional tracking. If you have been targeted by a similar exploit, do not hesitate to reach out. ChainBounty's Victim Relief Program provides the forensic evidence needed for law enforcement reporting and exchange cooperation.

👉 Apply for Victim Relief Program: https://chainbounty.io/en/event/campaign-victim-support/
(Disclaimer: This report is based on on-chain data and public OSINT. Identity-related content is circumstantial estimation. Final legal judgments must be confirmed through lawful procedures by law enforcement agencies.)
28 reads